🚀 Introducing: new architecture for database and API integrations, plus user logins and permissions
At Plasmic, we've been pursuing a vision of empowering anyone to create software.
Today, we're excited to share early access to new features that will enable a new class of dynamic websites and rich applications. Let's dive in.
Key highlights:
Back-end architecture for reading and writing data against APIs, databases, and other integrations within Plasmic Studio.
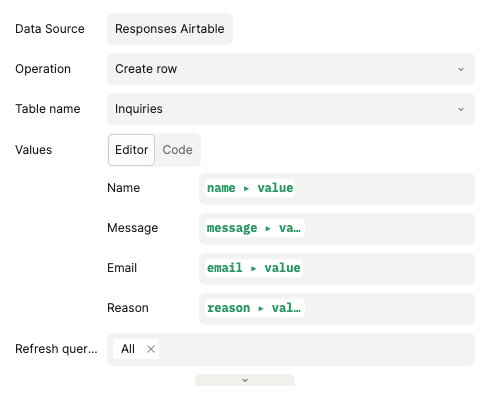
Built-in integrations (Airtable, PostgreSQL, Zapier, HTTP APIs)
User Logins for controlling who can access your app
New back-end architecture for database and API integrations
You can now read and write data against APIs, databases, and other integrations, all within Plasmic Studio. This goes beyond what code components enable—for instance, you can write as well as read, use authenticated sources like Airtable, directly query SQL databases, use a richer query builder UI, and lower reliance on code.
Now, you’re also able to use deep conditional filters to retrieve data that meets specific criteria. For instance, searching through a database of customer orders and identifying all orders that were placed in the last week.
We've launched the first set of integrations to support this release, including:
Airtable
PostgreSQL
Zapier
HTTP APIs
Let us know which integrations you’d like to see next.
How it works:
Fetch data from a relational database, or write arbitrary SQL queries:
Create or update records based on form inputs:
Build HTTP API requests, now with a full configuration and preview UI:
Make a button trigger a Zapier workflow to send emails:
And more!
You can add operations to any interaction, such as a button click, or to any page or component.
For example, in a task management app, you can add a data fetch to a page to retrieve a list of tasks. Then, you can add a button with an interaction step that creates a new task.
A key feature of this new architecture is that operations can be securely run server-side and integrated with auth (read more below).
Secure your app with authentication and permission roles
With authentication, you can ensure that only authorized users can access your app and its features. Plasmic now enables you to add user logins to your app, making it easy to verify the identity of your users and protect your data.
You can also set role-based permissions by assigning different levels of access to groups of users. For instance, you might want to give your sales team full access to your CRM app and limit other employees to just viewing the data in that app. Or, create custom roles for administrators with more advanced permissions.
Beyond role-based permissions , you can also secure your app by ensuring that users are only able to access specific data—for instance, ensuring each sales rep can only update the accounts they’re assigned to.
How it works:
To get started, click the ellipsis by the project name, and select “Configure app authentication.”
Afterward, in your app, you’ll see a currentUser variable available in dynamic values. You can use currentUser as a dynamic value in all the usual ways—for instance, conditionally show/hide content based on the current user.
Wherever you are using a backend operation, you can designate that it’s restricted to only specific roles, or that it should only access specific records based on currentUser.
Plasmic has a first-class auth provider, so users can easily sign in to your app via Plasmic, with minimal configuration. Alternatively, you can also use other providers, such as Supabase Auth, Auth0, or Okta. Documentation for this is coming soon.
Early access to these features is now available to all Plasmic users. Feel free to share your feedback with us in the Slack community. We’re excited to hear from you!